Tech Talk: More than you ever wanted to know about malware
Welcome to Tech Talk, a weekly column about the things we use and how they work. We try to keep it simple here so everyone can understand how and why the gadget in your hand does what it does.
Things may become a little technical at times, as that’s the nature of technology — it can be complex and intricate. Together we can break it all down and make it accessible, though!
Tech Talk

How it works, explained in a way that everyone can understand. Your weekly look into what makes your gadgets tick.
You might not care how any of this stuff happens, and that’s OK, too. Your tech gadgets are personal and should be fun. You never know though, you might just learn something…
What is malware?

You know it’s something bad, but do you really know what malware is? It’s probably not exactly what you’re thinking.
Malware is defined as any software designed to disrupt or exploit a device, a network, or data on either. Some shady bootleg app that steals your bank info is malware, but under this definition, so is Chrome or Microsoft Edge. You need to go one step further and describe malware as a thing that does this without your permission.
The easiest way to describe it is with a simple example: a boring flashlight app. You download and install a flashlight app to do only one thing: turn on your camera flash when you tap the icon. To do this, the app only needs access to the basics — an ability to take user input and send a request to toggle the flash on and off.
Now imagine the same app, but this time it wants to access your contacts. It doesn’t offer any sort of community access to your camera flash and doesn’t have a reason for doing it. It just does and you have no idea why. That’s malware. It’s planning on doing something with your data, maybe in the future, but the important thing is that it’s trying to do things it doesn’t need to do. Substitute any other data for your contacts and the situation is the same.
How does malware spread?
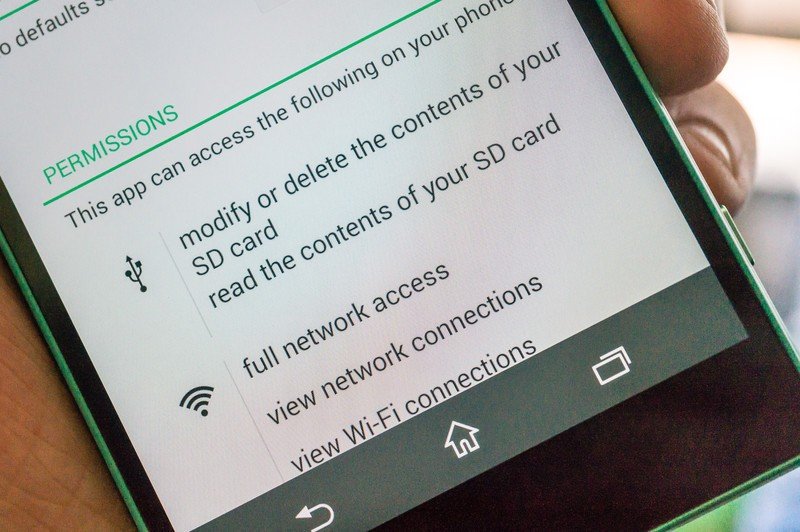
Thankfully, it’s very difficult for any application to do what’s described above in secret. Unfortunately, it probably doesn’t need to be secretive because you never looked to see what else the app tells you it will do down in its fine print.
One way malware is distributed is by relying on you to accept all the things an app can do without reading anything. However, this method only works for apps that follow the complicated and often silly platform distribution rules. And yes, that flashlight app scenario happened on both Android and iOS, in each official app store; it followed the rules, so it was allowed to at the time.
Social engineering (getting you to click yes, knowing you won’t read it all is social engineering at the lowest level) is probably the most common way to spread malware. If I can build an app that does things it shouldn’t, I still would need a way to have you install it. Trickery works because most people don’t realize the harm that can arise from their simple actions. You can compromise your information, your friends and family’s information, and even the information of other devices using the same network as you. All you have to do is click yes.
A scarier way of spreading malware is by exploiting bugs in your phone’s OS and installing software without your knowledge. Maybe you visit the wrong website, try pirating sites for “free” paid apps, or even connect to the wrong open Wi-Fi network. These are ways malware can find its way onto your device.
Once in place, this sort of malware can cause serious issues. Governments of the world even try it, so it can monitor the people they think need to be monitored because it’s powerful and usually undetectable.
What can I do to try and prevent all this?

Thankfully, it’s not that difficult to protect yourself. You could install one of the many malware scanners available and hope it catches any and everything, but you also need to follow a few simple rules if you just want things to be easy and malware-free.
Only use the official app store that came with your phone. Your phone comes with at least one way to find and install apps to do fun and cool things with. These stores aren’t perfect, but they are a million times better at catching and removing malware before it can get to you than any other distribution model. Apple tests every app before it’s placed in the store, while Google makes sure the app follows the rules before it’s made available, and then scans every app before it gets installed on your phone. Samsung, Epic, and other app markets also have safeguards in place to make sure they aren’t spreading bad apps.
Never click yes before you read what you’re agreeing with. This can’t be stressed enough! These user agreements are terrible and often full of language designed to give one party an advantage in the case of a dispute but force yourself to read through them every single time. You might not like your options; you’ll either need to agree to the terms presented or not use an app, a service, or even a device itself. Nobody wants to put their Galaxy S25 back in the box to send to Samsung because they don’t want Samsung to analyze the way they use it, but those are the rules. Once you’ve said yes, they can and will do what they asked permission to do. Make sure you’re OK with it all by reading what is put in front of you. (Editor’s note: You can trust companies like Samsung, Apple, or even Google to do only what they say they will do with anything they collect from your phone, so don’t let that scare you off.)

Always accept updates. When you buy a device you’re given a promise of software support for a specific amount of time. A big part of that support is patching the bugs and exploits used to hijack your phone or install bad apps without your knowledge. Trust that companies like Google and Apple know what they are doing but also accept that other smart people are trying to find ways to defeat every protection you have. Exploits will happen and when those get patched, be sure to install the update right away.
Never trust anything without verifying it first. This is the hardest part. Is that message really from your little brother asking for $200 or saying he forgot the gate code or is it from someone else? Make sure. The same goes for any links you come across — are you sure you can trust them? Be very cautious using public Wi-Fi networks, too. It’s easy to make one (you can do it right on your phone!) and with the right tools everything sent on them can be collected: passwords, 2FA information, credit card info, etc. Taking a minute to make sure you know the who and what is a lot easier than trying to fix everything after someone steals your identity or your credit card number.
Really, it’s not as hard as it sounds to protect yourself. It’s also not foolproof — anyone can end up with malware, even security professionals or government officials with security teams. Doing your part makes it a lot harder.













Post Comment